How To Create Assume Role In Aws
AWS Cross-Account AssumeRole Support
Overview
Avi Vantage can be deployed for Amazon Web Services (AWS) with multiple AWS accounts utilizing the IAM AssumeRole functionality. IAM roles provide access across AWS accounts to the AWS resources/API from the respective accounts, instead of sharing user Access Key ID and Secret Access Key from different accounts.
While creating the AWS cloud-type, new option of Use Cross-Account AssumeRole is available on Avi Vantage. The Use Cross-Account AssumeRole feature can be enabled if the AWS cloud needs to be created in an AWS account other than the one that hosts the Avi Controller.
Use Case
Referring to the below diagram, consider a hypothetical organization XYZ Corp with multiple AWS account IDs:
- IT – 123456789012
- Prod – 112233445566
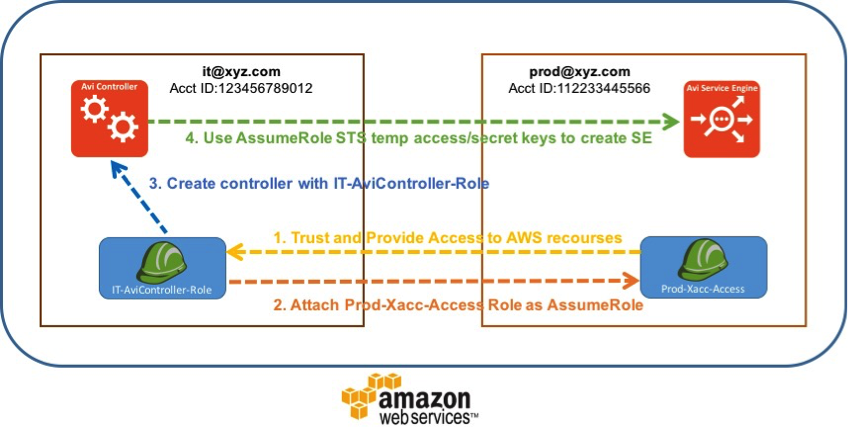
In a general deployment, the XYZ Corp would require an Access Key ID and Secret Access Key to create Avi Vantage Service Engine cloud in AWS for each account. Sharing the AWS access keys for respective accounts would be a security concern with this. In addition to this, it would be cumbersome to track all the keys and update them. Instead AWS IAM Roles can be used in every account. The IAM roles feature provides access to the AWS resources or API access across AWS accounts. These can be dynamic.
Prerequisites
The prerequisite configuration is required on AWS to set up the IAM user or roles to access other accounts using Assume Role.
Configuring Use Cross-Account AssumeRole
The Use Cross-Account AssumeRole feature can be enabled during the cloud creation step. Follow the steps mentioned below to enable the feature.
-
Navigate to Infrastructure > Cloud, click on create.
-
Provide the desired name of the cloud, and select Amazon Web Services as the Cloud Infrastructure Type, and click on Next.

-
Enable the Use Cross-Account Assume Role checkbox, available under the AWS User Credentials section.
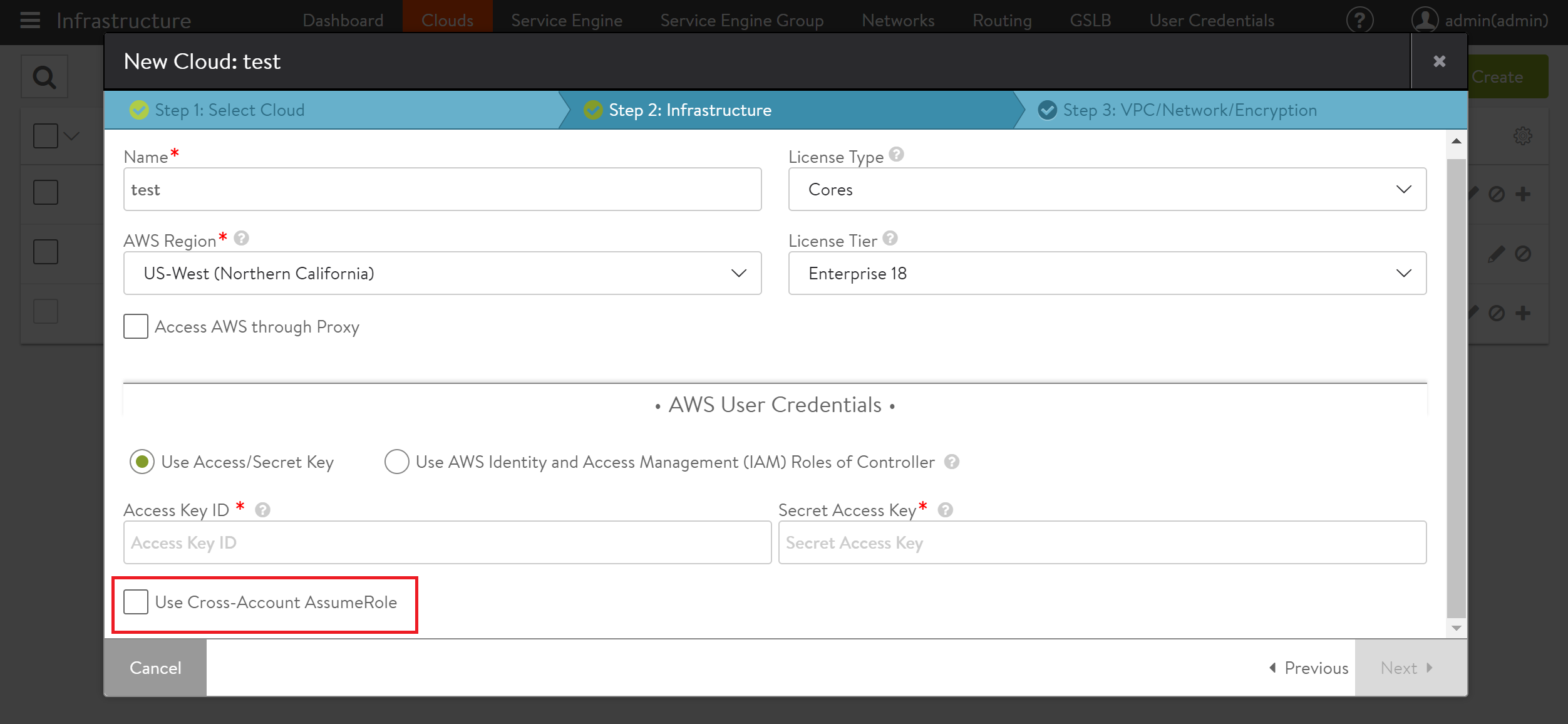
The configuration steps are divided into the following main points:
- Creating a role using AWS user interface
- Granting access to the role using AWS user interface
- Configuring Avi Vantage to use Use Cross-Account Assume Role for AWS accounts.
Configuring AWS
AWS accounts require access to AWS resources or APIs. In this example, Avi Controller is hosted in the IT account (AWS account id – 123456789012) and the Avi Service Engine cloud provides data path services in the Prod account (AWS account id – 112233445566).
Use the account IDs and resource ARNs that are applicable to your environment, while following this guide. Cross-account setup is explained in Delegate Access Across AWS Accounts Using IAM Role.
STEP-1: Creating a Role
In Prod account, set up the Prod-Xacc-Access role which will be a cross-account role.
-
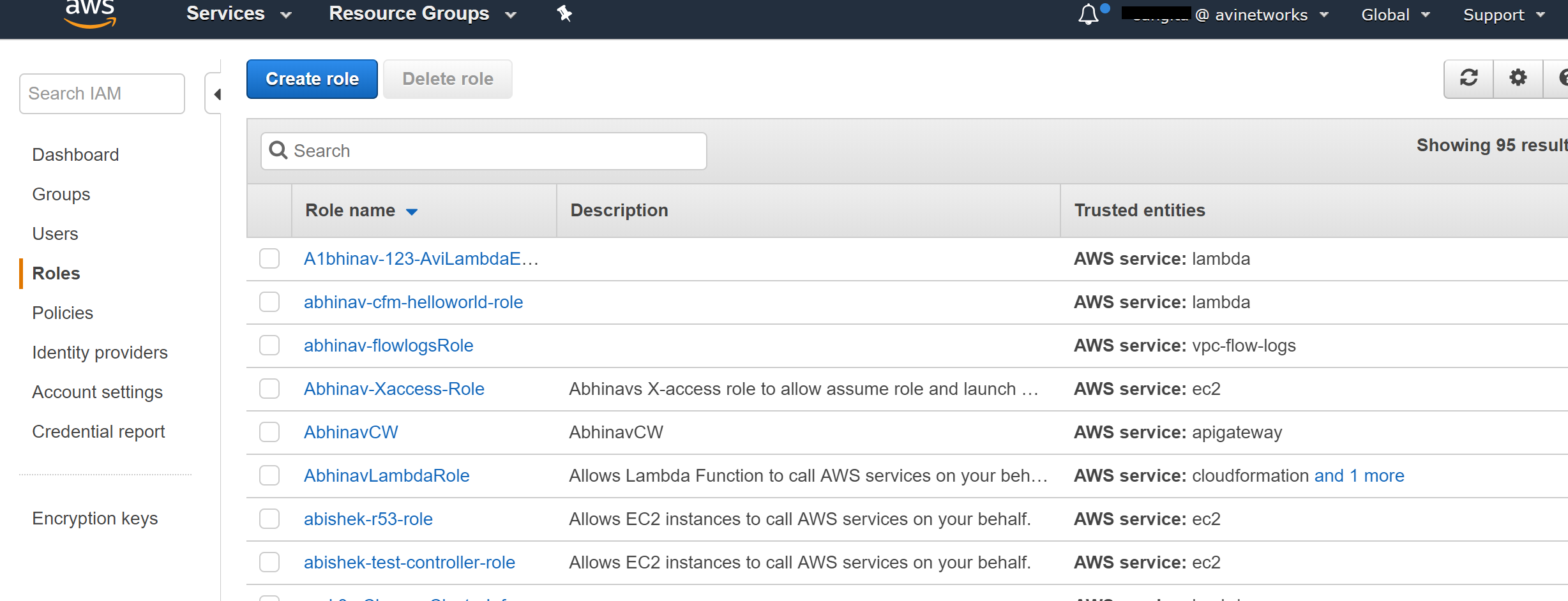
Navigate to IAM > Roles and click on Create New Role.
-
Select Another AWS account, and provide Account ID, and click on Next:Permissions. Enter the AWS account ID of the AWS account which can assume this role. In this example, it is the IT account (AWS account ID – 123456789012). You may choose Require MFA based on your requirement.
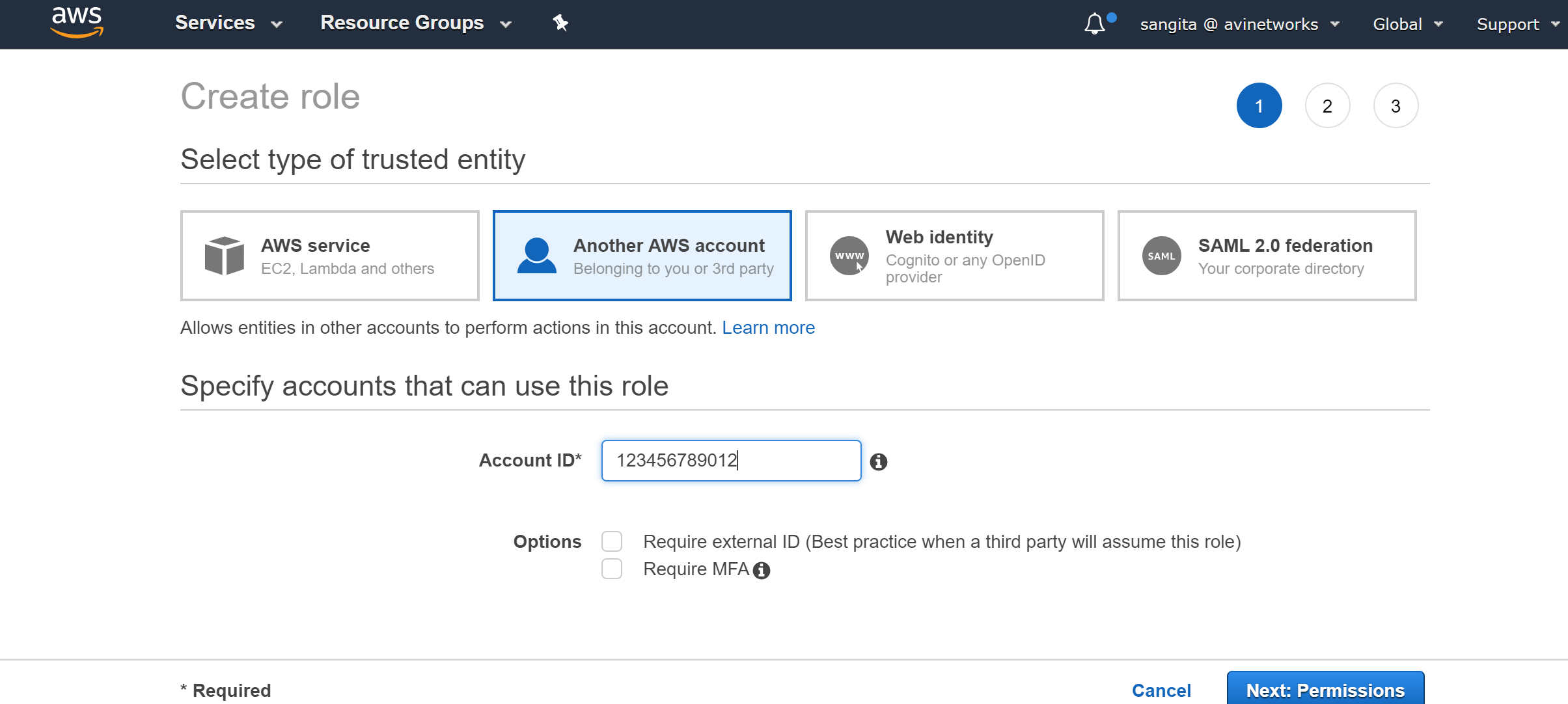
- Select the policies required by the Prod-Xacc-Access role to create the Avi SE for providing Avi Vantage functionality, and click on Review. The following are the policies attached to this role in this reference section:
- AviController-EC2-Policy
- AviController-IAM-XAccess-Policy
- AviController-R53-Policy
- AviController-S3-Policy
-
Provide the name of the role (Prod-Xacc-Access), the description (optional), and click on Create Role submit icon.
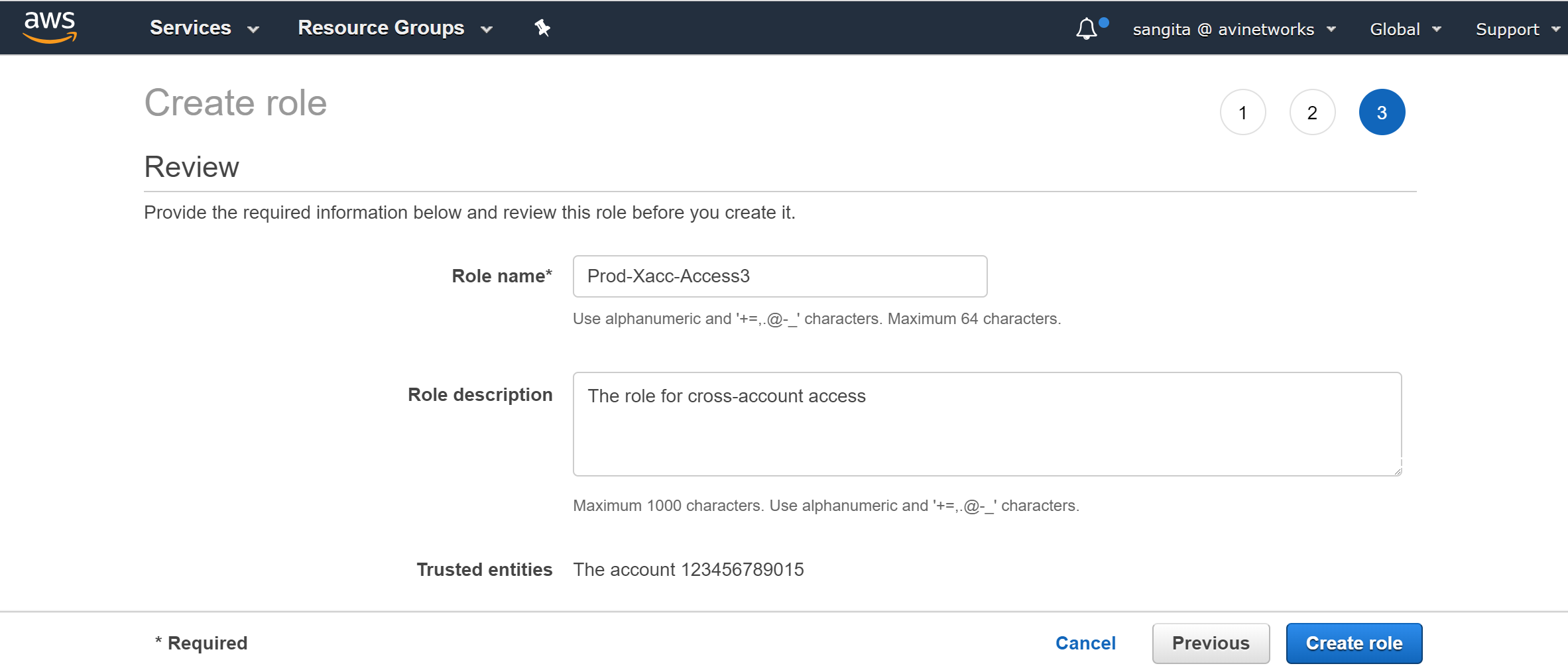
To summarize, for Prod-Xacc-Access role the role ARN will be displayed as arn:aws:iam::112233445566:role/Prod-Xacc-Access. Ensure that the format is: arn:aws:iam::account-id:role/role-name.
STEP-2: Granting Access to the Role
Once the Prod-Xacc-Access is set up in the Prod AWS account (112233445566), any user or role in the IT AWS account (123456789012) will be able to assume the role with appropriate configuration, as explained in the steps given below.
Create the IT-AviController-Role role in the IT AWS account (123456789012) to assume the role of Prod-Xacc-Access in the Prod AWS Account (112233445566). This is the role to which the Avi Controller instance will be attached.
Create the policy Cross-Account-AssumeRole-policy, which will be attached to the IT-AviController-Role role.
-
Navigate to IAM > Policies, and click on Create Policy.
-
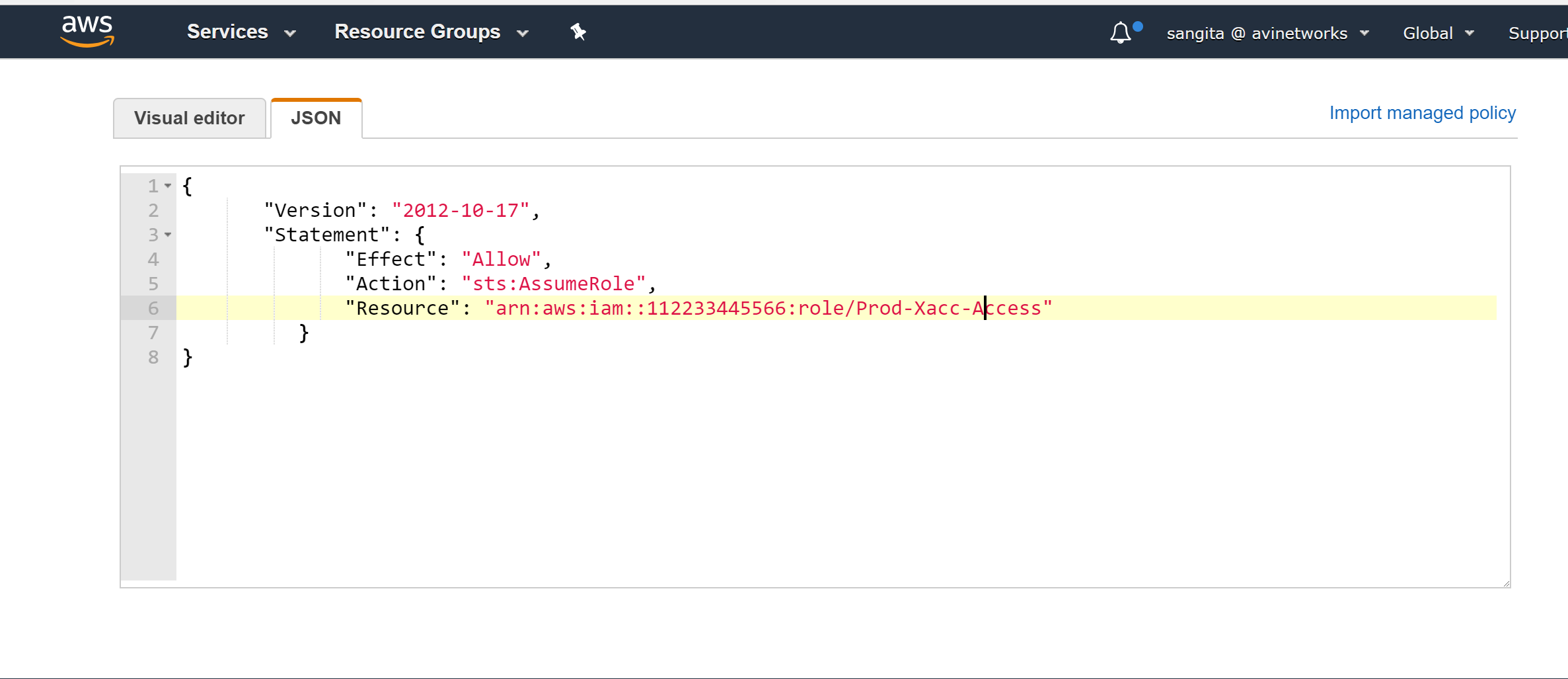
Configure the policy with sts:AssumeRole action and provide the resource reference for Prod-Xacc-Access role's ARN, which in this example is arn:aws:iam::112233445566:role/Prod-Xacc-Access.
{ "Version": "2012-10-17", "Statement": { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::112233445566:role/Prod-Xacc-Access" } } -
Navigate to the JSON tab, provide the following syntax, and click on Review Policy to save the policy.
For attaching multiple accounts, use the following policy syntax:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::<ACCOUNT-ID1>:role/<Role-Name-1>" }, { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::<ACCOUNT-ID1>:role/<Role-Name-2>" }, { "Effect": "Allow", "Action": "sts:AssumeRole", "Resource": "arn:aws:iam::<ACCOUNT-ID2>:role/<Role-Name>" } ] } -
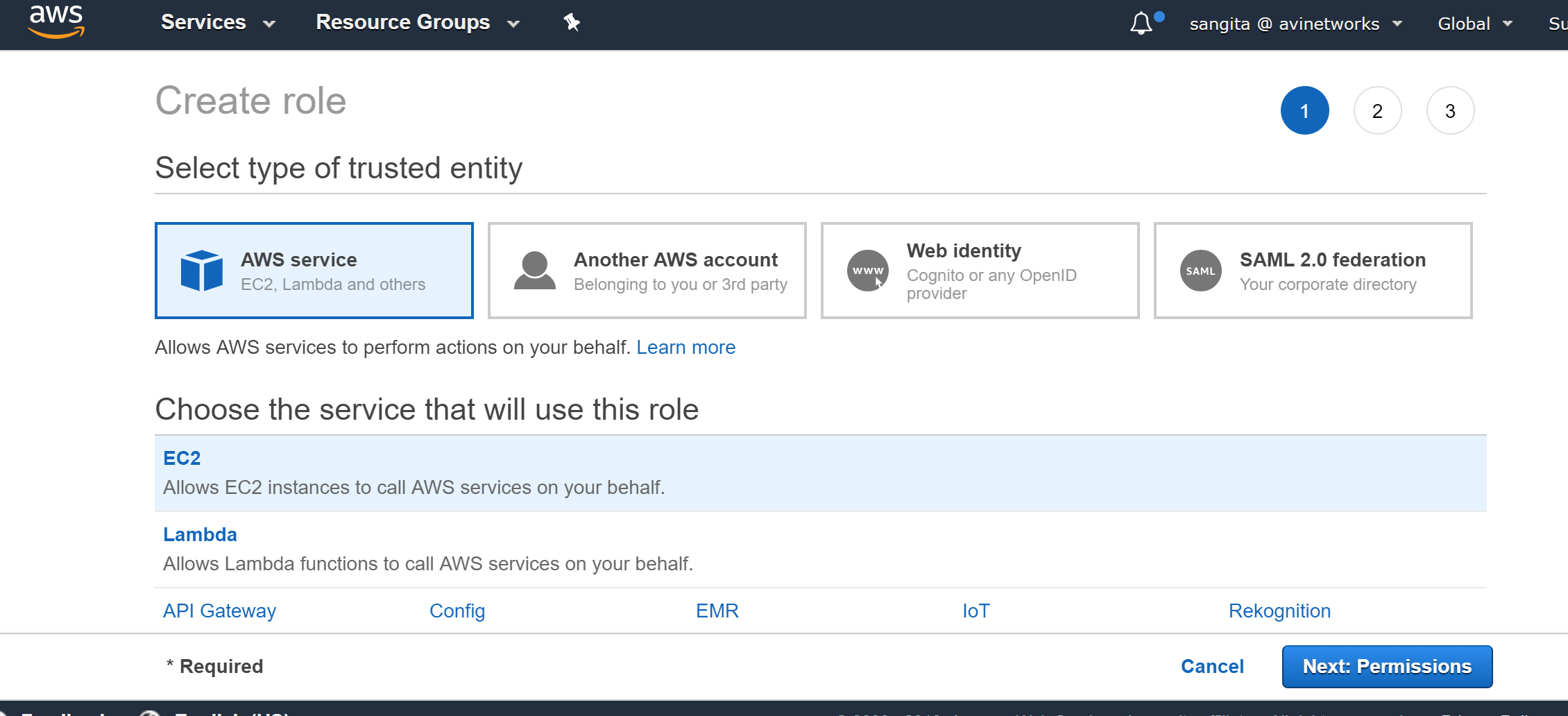
Navigate to IAM > Roles, click on Create Role.

-
Select AWS Service, select Amazon EC2 as the role type, and click on Next:Permissions.
-
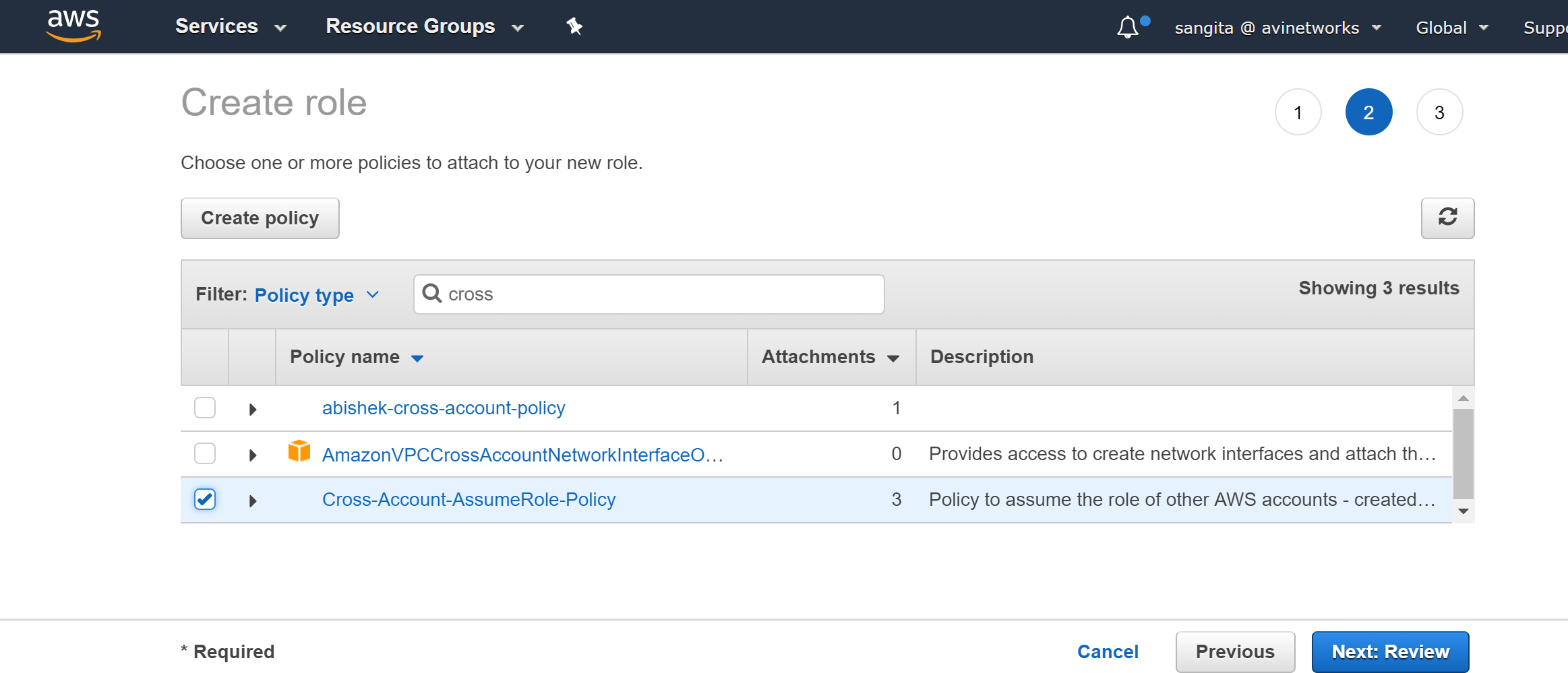
Under Attach-Policy, select the Cross-Account-AssumeRole-Policy created earlier and also the AviController-EC2-Policy, which is required for the Avi Controller's internal operations.

-
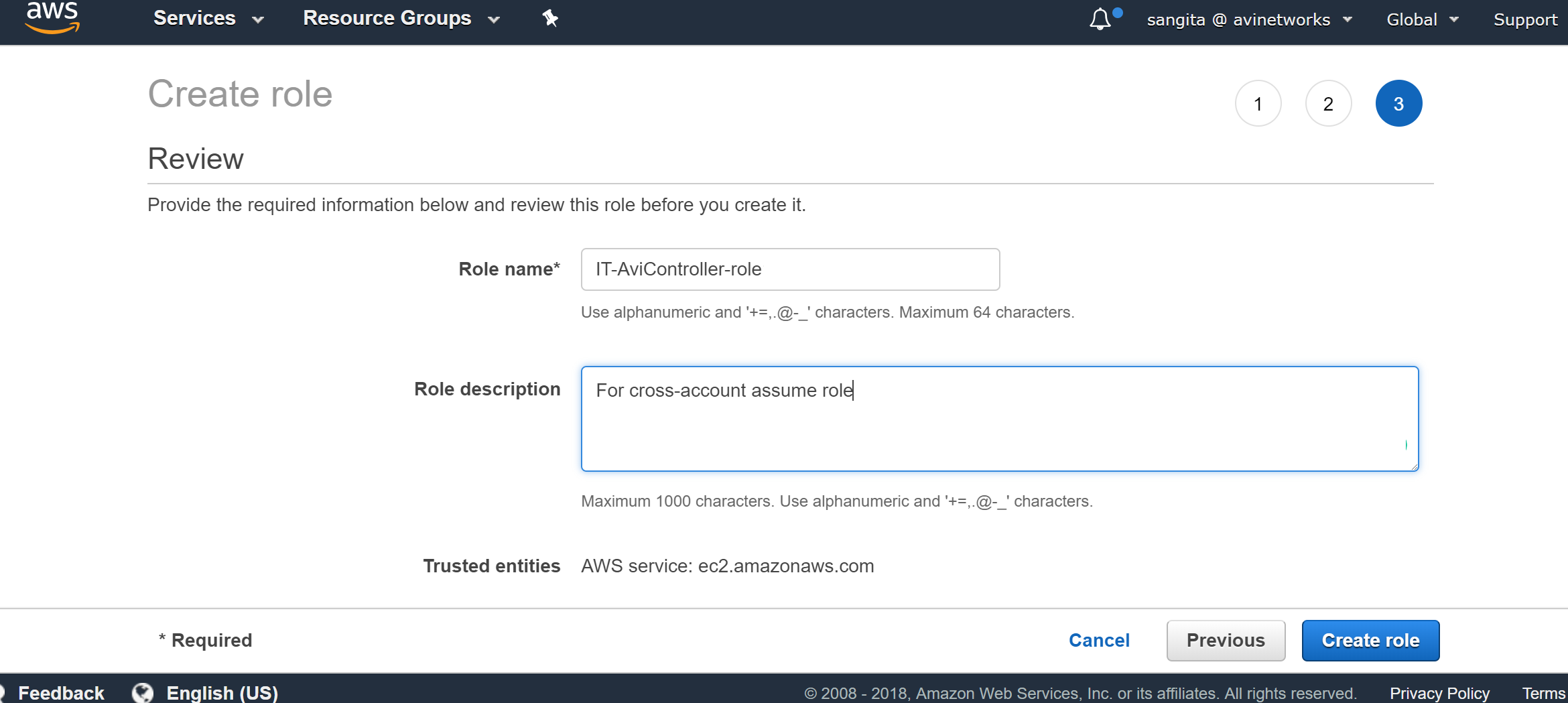
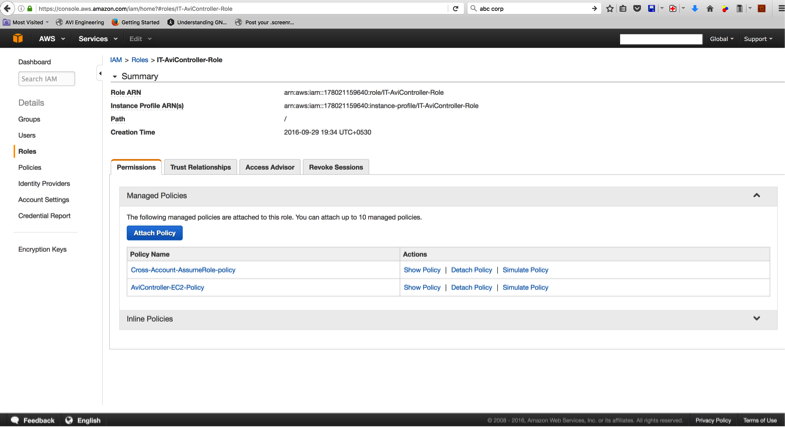
Provide the Role name as IT-AviController-role, the description (optional), and click on Create role. Verify if both policies are now attached.
Configuring Avi Vantage
After completing the prerequisite setup, you can configure the IAM role for Avi Controller as IT-AviController-Role by following the steps mentioned in AWS Installation Guide. Skip the cloud creation steps and choose No Orchestrator during the setup. Ensure that the VPCs and subnets are configured in AWS, so that Avi Controller management interface and Service Engine's management networks will be reachable from other accounts.
-
Create the AWS cloud by navigating to Infrastructure > Clouds and click on Create.

-
Choose the appropriate region and select the checkbox for Use AWS Identity and Access Management (IAM) roles. This will ensure that the IT-AviController-Role is attached to the Avi Controller when it is launched.
Note: Both IAM role and access/secret key can used for cross-account role given the role/user has the necessary permissions (cross-account policy).

-
Select the checkbox for Use Cross-Account AssumeRole, if the cloud has been set up in another AWS account. However, in this case, the Avi SE cloud is created in the Prod AWS account (112233445566) from the Avi Controller hosted in IT AWS account (123456789012).
As the cross-account AssumeRole has already been set up for IT-AviController-Role, on selecting the checkbox, the back-end APIs will fetch the associated AssumeRole accounts and their roles and display them in the drop-down list.
If there were no AssumeRoles attached, then the list would have been empty. There would be a text box that can be used to enter the ARN of the role for which the Avi Controller instance's IAM role (in our case, IT-AviController-Role) can assume the role. -
Select the ARN for the account and role, where the SE targets will be deployed.
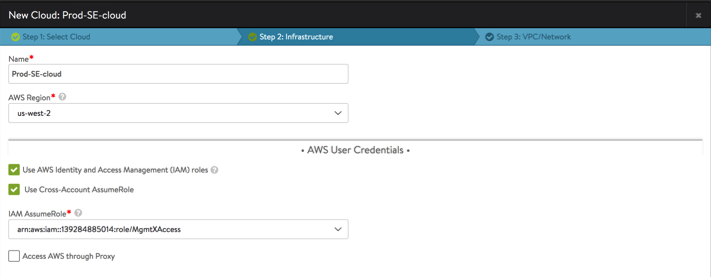
-
If the role has appropriate access and is correctly setup, Avi Controller will fetch the AWS account details and configuration's VPC networks. Similarly, this will continue for the older SE AWS cloud setup.
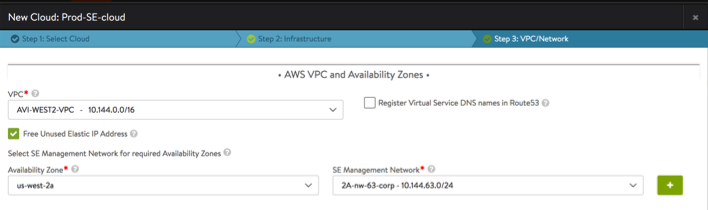
-
Cloud setup will progress, and the Avi SE AMI will be copied to the target account.
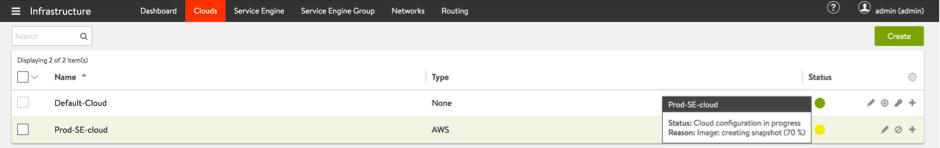
-
Once the transfer is completed, the cloud status will move to Cloud ready for Virtual Service placement.
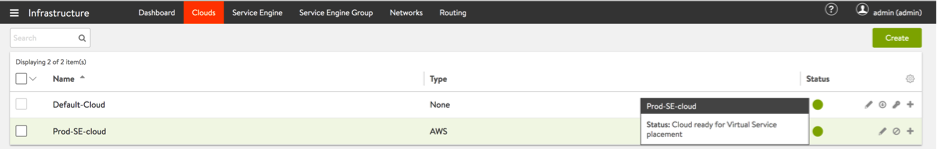
-
Virtual services can now be configured on this cloud by following the steps mentioned at Create a Virtual Service.
Additional Information
- AWS IAM
- AWS IAM Roles
- AWS IAM AssumeRole
- AWS Delegating API access using IAM Roles
- AWS IAM Tutorial on Delegate Access across AWS accounts using IAM Roles
-
AviController-EC2-Policy and AviController-R53-Policy are referenced in the IAM role setup guide.
-
AviController-IAM-XAccess-Policy
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Stmt1450417666000", "Effect": "Allow", "Action": [ "iam:GetPolicy", "iam:GetPolicyVersion", "iam:GetRole", "iam:GetRolePolicy", "iam:ListAttachedRolePolicies", "iam:ListPolicies", "iam:ListRolePolicies", "iam:ListRoles", "iam:ListAccountAliases", "iam:ListAttachedUserPolicies", "iam:ListAttachedGroupPolicies", "iam:GetUserPolicy", "iam:GetGroupPolicy", "iam:ListUserPolicies", "iam:ListgroupPolicies" ], "Resource": ["*"] } ] } -
AviController-S3-Policy
{ "Version": "2012-10-17", "Statement": [ { "Sid": "Stmt1450394113000", "Effect": "Allow", "Action": [ "s3:AbortMultipartUpload", "s3:CreateBucket", "s3:DeleteBucket", "s3:DeleteObject", "s3:GetBucketLocation", "s3:GetBucketTagging", "s3:GetObject", "s3:ListAllMyBuckets", "s3:ListBucket", "s3:ListBucketMultipartUploads", "s3:ListMultipartUploadParts", "s3:PutBucketTagging", "s3:PutObject" ], "Resource": [ "*" ] } ] }
How To Create Assume Role In Aws
Source: https://avinetworks.com/docs/latest/aws-cross-account-assumerole-support/
Posted by: kellyanowbod1944.blogspot.com

0 Response to "How To Create Assume Role In Aws"
Post a Comment